Protocol Design
Understanding how Pyth Entropy generates secure random numbers
The Entropy protocol implements a secure 2-party random number generation procedure. The protocol is an extension of a simple commit/reveal protocol. The original version has the following steps:
- Two parties A and B each randomly sample secret contributions to the random number, and .
- A commits to their number by sharing
- B reveals
- A reveals
- B verifies that
- The random number
This protocol has the property that the result is random as long as either A or B are honest. Honesty means that (1) they draw their value at random, and (2) for A, they keep a secret until step 4. Thus, neither party needs to trust the other -- as long as they are themselves honest, they can ensure that the result is random.
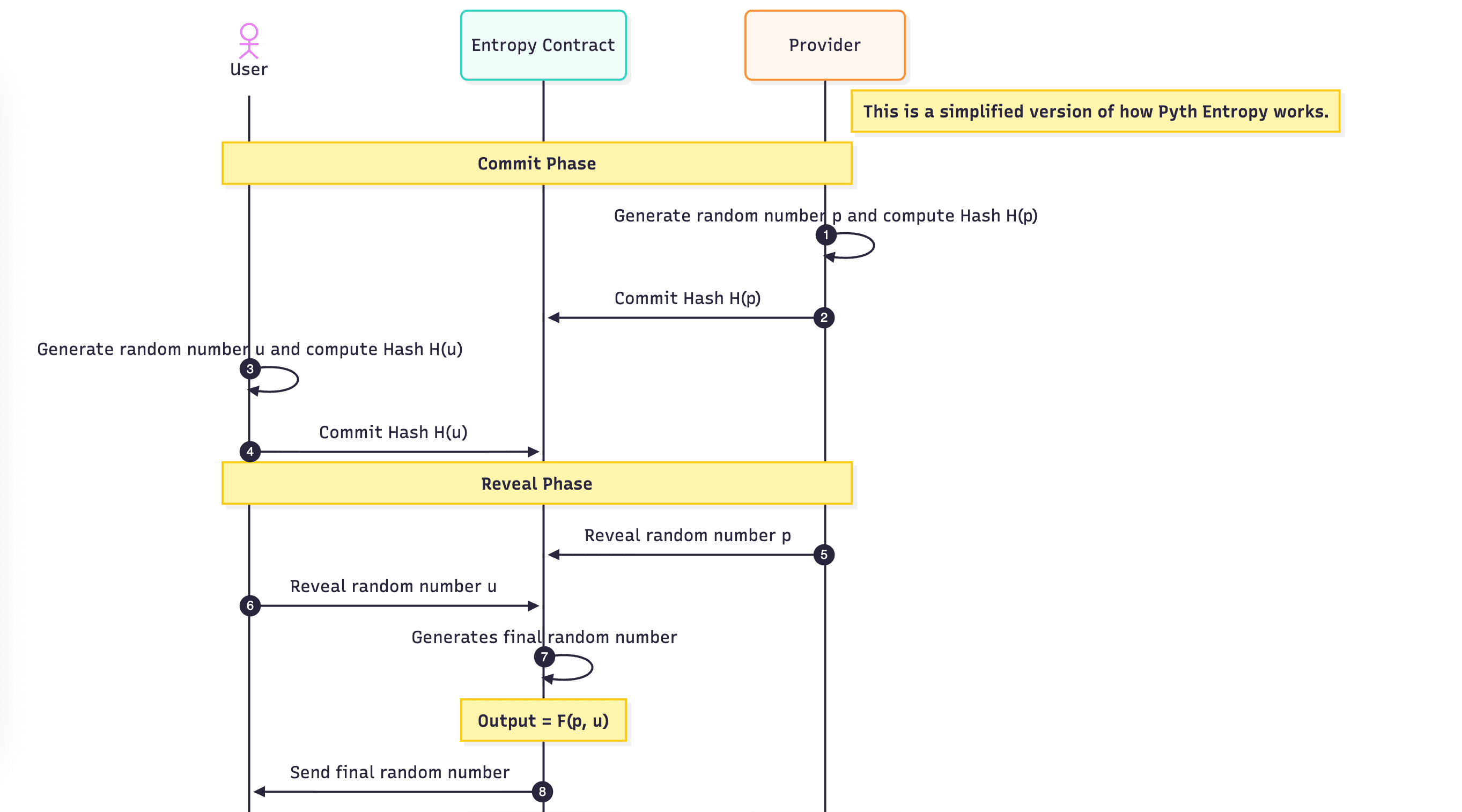
Entropy implements a version of this protocol that is optimized for on-chain usage. The key difference is that one of the participants (the provider) commits to a sequence of random numbers up-front using a hash chain. Users of the protocol then simply grab the next random number in the sequence.
Setup: The provider computes a sequence of random numbers, for :
The provider commits to by posting it to the Entropy contract. Each random number in the sequence can then be verified against the previous one in the sequence by hashing it, i.e.,
Request: To produce a random number, the following steps occur.
- The user randomly samples their contribution and submits it to the contract. (Users may also run this step using an on-chain PRNG if they trust the validator to not collude with the provider.)
- The contract remembers and assigns it an incrementing sequence number , representing which of the provider's random numbers the user will receive.
- After sufficient block confirmations, the provider submits a transaction to the contract revealing their contribution to the contract.
- The contract verifies to prove that is the 'th random number. The contract stores as the 'th random number to reuse for future verifications.
- If the condition above is satisfied, the random number .
- The contract submits a callback to the calling contract with the random number .
This flow is secure as long as several trust assumptions hold:
- Providers are trusted to reveal their random number regardless of what the final result is. Providers can compute off-chain before they reveal , which permits a censorship attack.
- Providers are trusted not to front-run user transactions (via the mempool or colluding with the validator). Providers who observe user transactions can manipulate the result by inserting additional reuests or rotating their commitment.
- Providers are trusted not to keep their hash chain a secret. Anyone with the hash chain can predict the result of a randomness request before it is requested, and therefore manipulate the result. This applies both to users of the protocol as well as blockchain validators who can use this information to manipulate the on-chain PRNG or reorder user transactions.
The code of default deployed provider can be found here.